Over the past several years, many businesses have made the decision to start using hardware security modules (HSMs). These hardware devices provide the highest level of security for sensitive data, offering tamper-resistance features and failsafe security measures that automatically destroy data if an unauthorized person gains access to the device. This makes HSMs an easy choice for InfoSec and DevSecOps leaders that take data security seriously.
However, most organizations are only using their HSMs for a small fraction of the possible use cases and are not taking advantage of their HSMs to their fullest potential. In this article, we’ll cover all of the ways that you can expand usage of these devices to bolster security throughout your environment and maximize ROI on your company’s decision to invest in HSMs.
Common Use Cases For HSMs
If your organization is like most of those using HSMs today, you’re probably only using your HSMs for a select few use cases. The usual suspects are the root of trust for internal PKI, TDE keys, TLS keys for web servers, and code signing keys. If you’re a financial processor you may also use them to protect PCI data. These are all great use cases but they only represent the tip of the iceberg of your HSMs’ capabilities.
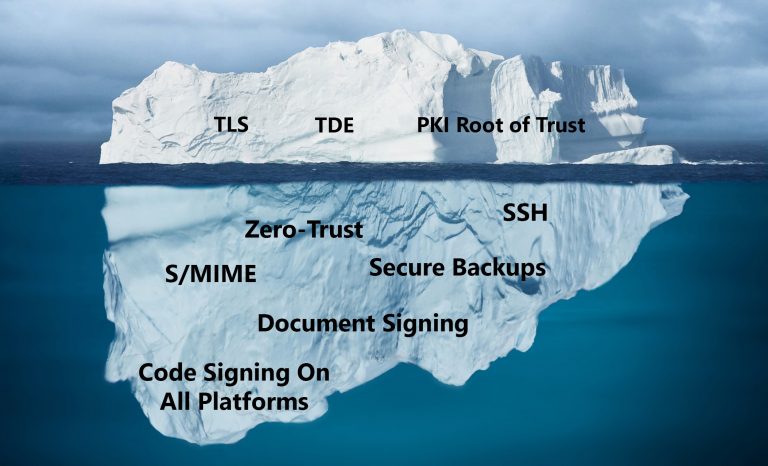
That fact is that HSMs and key managers are severely under utilized in most businesses. In order to really take advantage of hardware security modules and increase the ROI, enterprises should seek to keep all cryptographic key material inside their HSMs, regardless of use case. With the increased adoption of cloud computing, this is even more important today than it has been in years past.
Getting The Most Out Of Your HSMs
Cryptographic keys are used everywhere these days, whether you are aware of them or not. Corporations that already use HSMs have the ability to use these devices to protect the confidentiality, integrity, and non-repudiation of every aspect of their business, with the right cryptographic software in place.
This means it’s possible to use HSMs for these additional use cases:
- Storing SSH keys
- Securing email via S/MIME or PGP
- Protecting backups before they’re moved to the cloud
- Signing documents
- Securing keys used for zero-trust implementations
- Signing code for all platforms
- Protecting data in transit
- and more.
Challenges With Expanding HSM Usage
So, why aren’t businesses using HSMs for all possible use cases? The answer comes down to the ROI on the development hours needed to enable them.
In particular, a business would need to develop cryptographic software to interface with both end-user clients and the HSMs themselves to enable new use cases. HSMs typically expose lower-level cryptographic APIs (e.g. PKCS11, JCE, or CAPI/CNG) which require specialized skills to develop against. Typically, this type of development is not a core competency of the business that needs the solution. As a result, developing this solution in-house is a costly and error-prone endeavor.
Making matters worse, the degraded performance that typically comes with poorly written “bootstrapped” cryptographic software can lead to bottlenecks in the CI/CD pipeline. Use cases involving lots of transactions and/or large volumes of data can further degrade performance on poorly implemented integrations.
Ultimately, most companies opt to not build these types of cryptographic solutions. This decision, in turn, means that most companies aren’t getting the most out of their HSMs and are opening up the door to potential security vulnerabilities.
A Turnkey Solution For Expanding Usage Of Your HSMs
What if there were a way to overcome these obstacles? Would HSM adoption rise? Would businesses get more out of their HSMs while also strengthening security?
We believe so, and that’s why we created GaraSign.
GaraSign is a cryptographic processing platform that provides all the native client integrations you need so you can integrate your HSM directly with the tools you use today. It’s a turnkey solution that doesn’t require any custom development, enabling you to immediately get more usage out of your HSMs. Additionally, via techniques like hash signing, performance is no longer an issue.


