Transport layer security (TLS) is the industry standard protocol for securing data in transit. Two of the biggest challenges with TLS are protecting the TLS keys and managing their certificates. TLS keys are often stored in software directly on web servers, leaving them vulnerable to compromise. For large enterprises managing many servers, this creates serious risk and makes certificate lifecycle management difficult.
With GaraSign, TLS keys are secured in a hardware security module (HSM), rather than in software or stored locally on servers. Avoiding outages with timely rotation of certificates is greatly simplified, as all keys, certificates & code signing solutions are centrally managed in the HSM.

The industry standard for enterprise organizations is to encrypt all network traffic with Transport layer security (TLS). For enterprises, this presents two challenges: the TLS keys must be secured, and the certificates must be renewed before expiration to avoid outages and downtime.
All too often, TLS keys and certificates are stored locally in software on servers. This doesn’t provide adequate security, nor does it enable easy certificate rotation, as the certificates are not centrally managed.
Storing TLS keys in software on end-point devices and servers leaves them vulnerable to compromise by attackers.
Secure sockets layer (SSL/TLS) certificates must be renewed to avoid outages, but it's hard to do so when they aren't centrally managed by a hardware security module (HSM).
Many servers means many keys, making it difficult to remain compliant and meet TLS key management requirements.
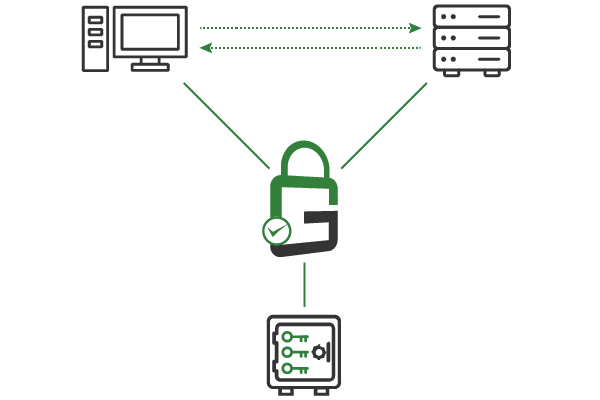
GaraSign is deployed on customer-managed infrastructure between the HSM and the servers, restricting those servers to proxied key access.
The result is that TLS keys remain secured and non-exportable in the HSM, while servers can use the keys they need to perform transport layer security (TLS) handshakes and protect network traffic. GaraSign further secures HSM keys via granular access controls and features, such as device authentication, IP address whitelisting, and more.
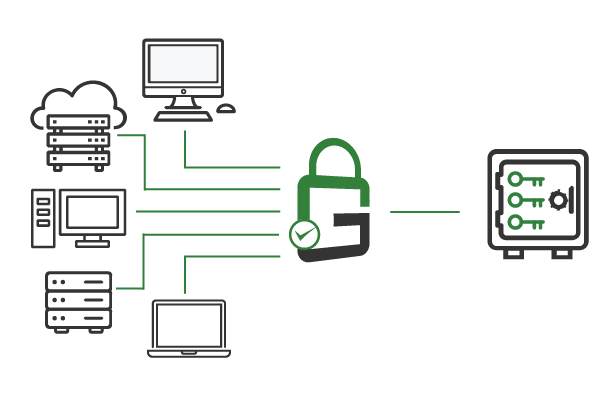
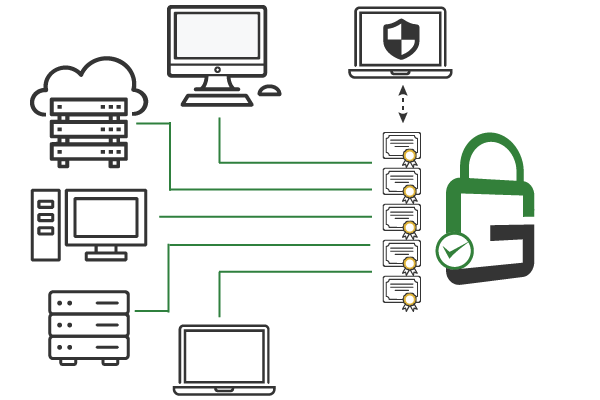
When you deploy GaraSign, all transport layer security (TLS) certificates are centrally managed in the hardware security module (HSM) software. This ensures easy certificate rotation to prevent outages and costly downtime. It’s also easy to perform other certificate lifecycle management tasks.
No matter how many transport layer security (TLS) keys and TLS certificates are in a given environment, GaraSign enables enterprises to manage and audit their infrastructure from a centralized hardware security module (HSM) software location. Using this HSM as a service approach, administrators always maintain complete visibility on all TLS keys. GaraSign creates a detailed log for each TLS key, making it easy to audit key usage to see when these TLS keys were used, at what time, and by which users.
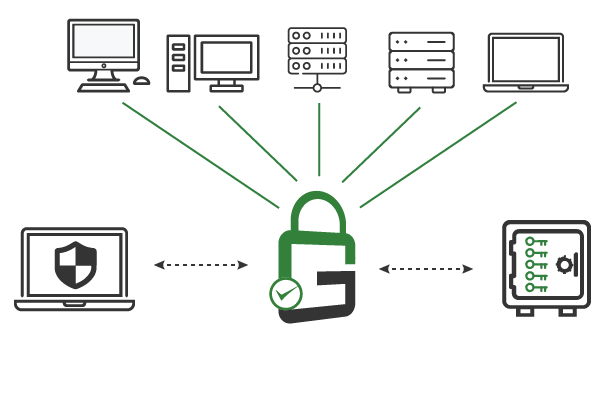
GaraSign can also manage the TLS keys and certificates for client authentication (aka mutual TLS). This can enable privileged access management (PAM), via features like multi-factor and device authentication (MFA), without reconfiguring servers.
The main benefit is that the sensitive private hardware security module (HSM) keys are never exported. There are additional benefits: HSM certificate management can be automated, and advanced security controls can be implemented on the HSM keys.
GaraSign supports both. Web applications should have their transport layer security (TLS) keys protected by GaraSign to ensure attackers can’t impersonate them by stealing the private TLS key. Clients that use Mutual TLS should have the client’s private key protected by GaraSign to provide centralized auditing, automated TLS certificate management, and seamless deployment of additional cybersecurity controls.
While an extra network hop is added, the performance impact is minimal since this hardware security module (HSM) key is only used during the initial TLS handshake. After the handshake is complete, GaraSign is no longer needed.
When using mutual transport layer security (TLS), GaraSign can proxy the client TLS key used to complete the challenge-response handshake. With the TLS key behind GaraSign’s privileged access control, GaraSign can enforce additional cybersecurity controls, e.g., multi-factor authentication (MFA), before it allows the use of the hardware security module (HSM) key. In other words, the web application delegates the additional cybersecurity controls to GaraSign and is unaware that the additional privileged access controls are taking place.
Yes. GaraSign can transparently enforce privileged access cybersecurity controls such as MFA without any new coding. Just turn on client-certificate authentication (either at your web server, load balancer, or some other proxy) and store the client private hardware security module (HSM) keys in GaraSign. Then, for each transport layer security (TLS) key, set the policy to one that requires MFA (or any other privileged access security control you would like to enforce).
GaraSign can automate the renewal process and make sure the clients and servers have the new hardware security module (HSM) certificates they need. For extremely sensitive environments where HSM certificate automation is not permitted, GaraSign can alert administrators about certificates nearing expiration, and they can decide what actions to take.
Schedule a demo to see how GaraSign can improve the security and performance of cryptographic operations throughout your environment.
321 Tenth Ave #1208
San Diego, CA 92101
(858) 751-4865
info@garantir.io
Copyright © 2023 Garantir LLC. All Rights Reserved.