Integrations To All The Tools You Use
GaraSign comes with a host of native client integrations, simplifying deployment and eliminating the need to develop custom integrations or install new software on endpoint devices.












There are many excellent enterprise cybersecurity tools to choose from. Some are managed on-premise, others are consumed as a service, and others still use a hybrid model. The challenge enterprises face is not a lack of cybersecurity tools or solutions but rather a lack of seamless interconnectivity between these privileged access management (PAM) tools and a single place to manage and audit them.
GaraSign is a cybersecurity platform that allows enterprises to securely and efficiently integrate their security systems in a way that does not disrupt existing business processes. By factoring out what’s common, GaraSign can centralize and simplify the management of your enterprise’s most sensitive areas, including PAM, privileged identity management (PIM), secure software development, code signing, data security, public key infrastructure (PKI) & hardware security module (HSM) solutions, DevSecOps, and more.

Enterprise cybersecurity leaders must attend to data security, privileged access management (PAM), privileged identity management (PIM), secure software development, secure code signing, email security, and much more. There is a single innovation common to all of these security needs: public key cryptography.
With public-private key pairs enabling so many dimensions of cybersecurity, enterprises can unify their strategy by centrally securing and managing all of the private keys in their environment. The challenge is protecting the keys without obstructing access, introducing performance bottlenecks, or creating integration challenges.
If private keys are stored in software on endpoint devices, they are relatively easy for attackers to compromise, creating unnecessary risk and compliance challenges for the enterprise.
Cybersecurity is a top priority but it can't come at the cost of performance. Enterprises demand that keys are secured while keeping up with the tempo of everyday operations.
When private keys are properly secured in a hardware security module (HSM) or key manager, integration challenges arise, as many common platforms are not natively supported.
Schedule a demo to see how GaraSign can improve the cybersecurity and performance of cryptographic operations throughout your environment.
GaraSign is a cybersecurity orchestration platform that supports data security, privileged access management (PAM), privileged identity management (PIM), secure software development, secure code signing, public key infrastructure (PKI) and hardware security module (HSM) solutions, email security, and more.
Schedule a demo to see how GaraSign can improve the cybersecurity and performance of cryptographic operations throughout your environment.
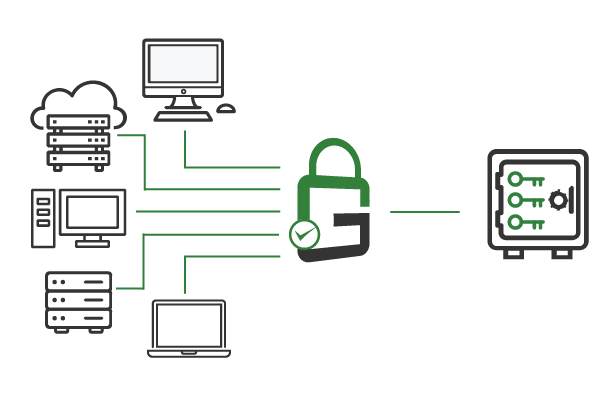
GaraSign is deployed on customer-managed infrastructure between the HSM and the clients, restricting all clients to proxied key access.
The result is that HSM private keys remain secured and non-exportable in the HSM at all times, while authorized end-users can still use the keys they need without interfacing with the HSM directly.
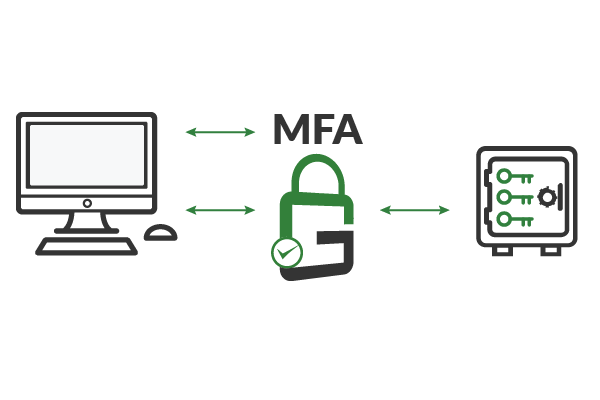
Because clients authenticate to GaraSign, rather than the hardware security module (HSM), customers can enforce granular controls, including multi-factor authentication (MFA), privileged access management (PAM), privileged identity management, device authentication, approval workflows, and more, without needing to manually reconfigure servers or modify applications.
These additional security features can be enforced for any use case— secure shell (SSH), secure code signing, transport layer security (TLS), public key infrastructure (PKI), access to encrypted data or documents, and much more— on a per-key or per-user basis with a few clicks from the GaraSign admin interface.
Schedule a demo to see how GaraSign can improve the cybersecurity and performance of cryptographic operations throughout your environment.
GaraSign is built with a client-side hashing architecture. Clients hash the data they need to sign before sending it over the network to create the hardware security module (HSM) signature.
This architecture limits the amount of data being transmitted over the enterprise network, providing extremely high performance for all cryptographic operations, while the private keys remain in the HSM.
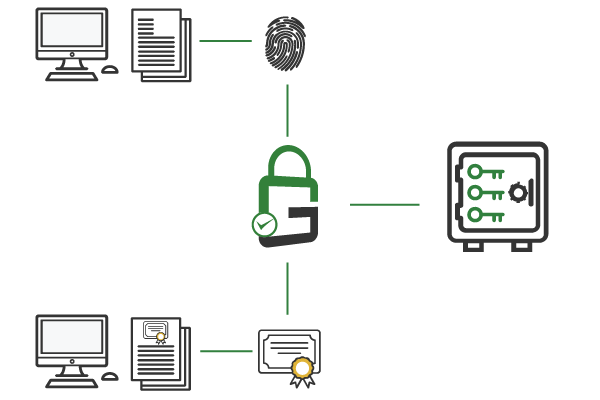
GaraSign supports all of the industry’s leading HSM and key manager vendors. It is even possible to use GaraSign with multiple HSMs from different vendors simultaneously, including cloud-based HSM and key management servers (KMS).
Deployed on customer-managed infrastructure, GaraSign can run on-premise, in the cloud, or in a hybrid infrastructure. GaraSign is easily deployed in any environment.
GaraSign comes with a host of native client integrations, simplifying deployment and eliminating the need to develop custom integrations or install new software on endpoint devices.












Check out these recorded demo videos to see GaraSign in action.
Schedule a demo to see how GaraSign can improve the cybersecurity and performance of cryptographic operations throughout your environment.
GaraSign supports all use cases based on cryptographic keys.
Sign code from any platform, including Apple, Microsoft, Linux, and much more.
Secure SSH keys in a hardware security module (HSM) and easily enforce granular access controls.
Enable transport layer security (TLS) with mutual authentication while private keys remain in an HSM.
Digitally sign documents using keys that are secured in your corporate hardware security modules (HSMs).
Sign and encrypt backups to prevent attackers from reading or altering data.
Encrypt application log files without modifying the application source code.
Automated certificate renewal across the enterprise to avoid outages.
No. When you deploy GaraSign, cryptographic keys are never exported from the hardware security module (HSM) or key manager. The HSM private keys are generated and stored in a non-exportable state within the cryptographic device.
Clients are restricted to proxied key access, meaning that clients make their cryptographic requests via GaraSign. GaraSign then authenticates and authorizes the client according to the policy in place, interfaces with the HSM to perform the cryptographic operation on the client’s behalf, and returns the finalized cryptographic data to the client.
GaraSign is deployed on customer-managed infrastructure and can run on-premises, in the cloud, or in a hybrid environment. All types of infrastructure are supported.
No. GaraSign is licensed to customers and deployed on fully customer-managed infrastructure, so the Garantir team never has access to your hardware security module (HSM) private keys or data.
GaraSign integrates with Thales Luna HSMs, Entrust nShield HSMs, HashiCorp Vault, AWS KMS, AWS CloudHSM, Google Cloud KMS, and Azure Key Vault. New integrations are added frequently so check in with the Garantir team if your HSM or key manager is not listed here.
Although GaraSign introduces an additional network hop in the architecture, the overall data sent over the network is drastically reduced via techniques like client-side hashing and enveloped encryption.
With client-side hashing, signing clients compute the hash of the data they wish to sign locally, then send the hash over the network to GaraSign, which finalizes the digital signature authentication by applying the private key in the cryptographic device to the hash. This keeps the data sent over the network to a minimum, regardless of the size of data being signed.
While it is technically possible to have clients interface directly with the HSM, deploying GaraSign brings several major benefits that would otherwise be difficult to achieve.
First, GaraSign integrates with all major tools and platforms to ensure fast and easy deployment. Clients are only required to interface with GaraSign (rather than the HSM), and GaraSign provides a multitude of native client integrations. Hence, the solution works end-to-end without any custom development work.
Second, because clients interface with GaraSign, it becomes much easier to enforce granular security controls, like multi-factor authentication, device authentication, privileged access management (PAM), privileged identity management (PIM), approval workflows, notifications, and more, that might not be possible with the HSM alone. GaraSign supports these granular access controls for a wide range of use cases. Policies can be established and enforced on a per-key or per-user basis with a few clicks from the GaraSign admin interface.
Third, not all HSMs and key managers allow granular access to different keys. In some cases, if you have access to a slot on the HSM, you have access to all HSM private keys on that slot. With GaraSign, more granularity is possible.
Strictly speaking, GaraSign does not enable new use cases for the HSM. Technically, an HSM can be used to secure any cryptographic key. The trouble is using the HSM keys at speed and scale from existing workflows without needing to export them from the HSM. This is where GaraSign comes in.
Because GaraSign provides all of the necessary native client integrations and ensures extremely high performance, it becomes practical to use HSM software to secure the keys for new use cases that aren’t typically considered appropriate for the HSM cryptographic hardware. An example will help illustrate this point.
Suppose you begin storing the secure shell (SSH) keys to access sensitive production servers in your HSM security module. How would authorized end-users access those keys when they needed to? Either the HSM keys would need to be exported from the HSM to the authorized end-user’s device, which defeats the purpose of storing them in the HSM to begin with, or the enterprise would need to build custom integrations from the SSH client (e.g. PuTTY, OpenSSH, WinSCP, etc.) to the HSM. The latter is a difficult, time-consuming, and expensive project. It may also introduce vulnerabilities, as a project of this nature is generally not an enterprise’s area of expertise. If the enterprise wants to enforce granular controls like multi-factor authentication (MFA) across a fleet of servers, it would require manually installing privileged access management (PAM) modules on each and every server individually.
GaraSign provides a plethora of native client integrations, and also ensures high performance, so it becomes feasible to store the cryptographic keys for any use case in the HSM software without needing to build custom HSM integrations or modify existing processes. Because clients authenticate to GaraSign, customers can enforce granular controls like MFA and device authentication with just a few clicks from a single interface.
All GaraSign nodes deploy in a high availability cluster. Through a combination of strong redundancy and minimal data sent over the network, GaraSign provides high assurances for uptime. Customers who desire “break glass” capabilities can configure GaraSign appropriately at deployment time.
Yes, GaraSign has a documented threat model. Get in touch with the Garantir team to request a copy.
Yes, GaraSign provides certificate lifecycle management features, including issuance, revocation, renewal, CSR generation, and more. This capability is available to all customers who deploy GaraSign for at least one use case.
Schedule a demo to see how GaraSign can improve the cybersecurity and performance of cryptographic operations throughout your environment.
321 Tenth Ave #1208
San Diego, CA 92101
(858) 751-4865
info@garantir.io
Copyright © 2023 Garantir LLC. All Rights Reserved.