Privileged access management (PAM) is a challenge for all organizations with a large workforce and many resources to protect.
GaraSign simplifies and strengthens PAM by enabling centralized management of digital identities and credentials, including the option to enforce granular controls without needing to make manual modifications to servers or applications.
In many ways, privileged access management (PAM) boils down to protecting and managing the credentials needed to access privileged systems and data. Web applications are accessed with transport layer security (TLS), requiring proper protection of the TLS keys. Sensitive systems are accessed via protocols like secure shell (SSH) and remote desktop protocol (RDP), meaning the SSH and RDP keys must be kept secure. Strong encryption is used to secure sensitive data, so the decryption keys must be protected. All of these keys should be safeguarded with hardware-level protection.
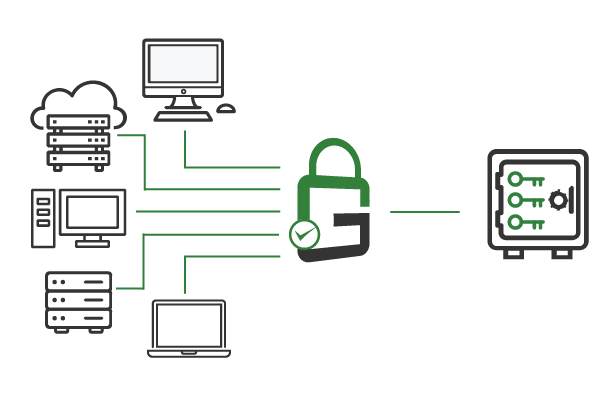
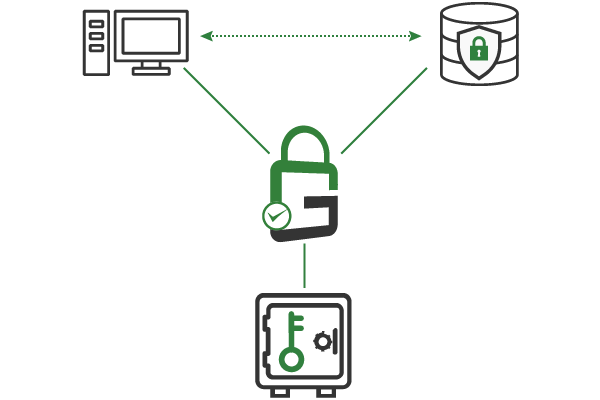
Because all digital identities and cryptographic keys are centrally secured and managed, select keys can be left in a disabled state until it’s time to use them. Decryption keys for sensitive data, secure shell (SSH) keys for privileged systems, code signing keys for production releases, and more should be disabled and activated only when they must be used.
GaraSign supports several granular controls, including multi-factor authentication (MFA), device authentication, approval workflows, and more. Clients authenticate to GaraSign when they request to use a key so that these granular controls can be enforced on a per-key or per-user basis with a few clicks from the GaraSign interface. There’s no need to reconfigure servers manually.
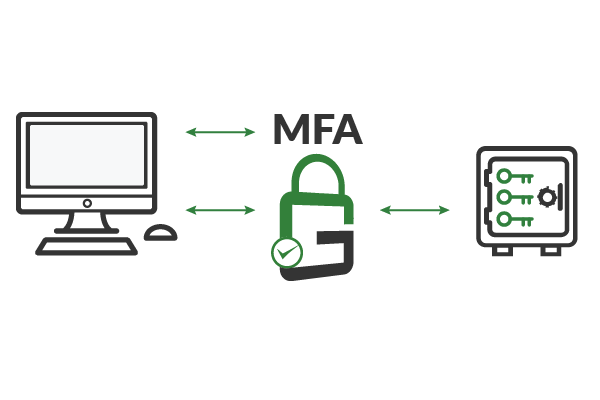
GaraSign drastically simplifies the process of creating and assigning digital identities. All certificates and keys, such as transport layer security (TLS) keys, are generated and stored within a centrally managed hardware secure module (HSM). Clients send requests to use a key to GaraSign, which then authenticates the client according to the set policies and, if approved, performs the private key operation on the client’s behalf. Granular access controls can be enforced on a per-key or per-user basis.
Create a digital identity for every client, be it human or machine, and store all certificates and keys in a centrally managed hardware security module (HSM).
Implement secure protocols like mutual transport layer security (TLS) and secure shell (SSH) to enforce key-based authentication whenever possible.
Enforce multi-factor authentication (MFA), device authentication, approval workflows, notifications, and more, on a per-key or per-user basis
All digital identities and keys are centrally secured and managed, so policies can be established from a single interface.
Leave sensitive keys disabled until seconds before an authorized and authenticated end-user needs access.
GaraSign supports Single-Sign On (SSO) using existing identity providers, resulting in fast adoption and easy deployment.
Schedule a demo to see how GaraSign can improve the cybersecurity and performance of cryptographic operations throughout your environment.
1041 Market Street #302
San Diego, CA 92101
(858) 751-4865
info@garantir.io
Copyright © 2023 Garantir LLC. All Rights Reserved.