SSH is used extensively throughout nearly every IT environment. While SSH brings many benefits, SSH access isn’t always adequately managed. It’s not uncommon to find SSH keys scattered throughout the enterprise on endpoint devices with limited security controls in place.
GaraTrust simplifies SSH key management by making it easy to store all SSH keys in a centrally-managed hardware security module (HSM) while providing end-users with remote access to the keys they need. With GaraTrust, you can easily grant and revoke SSH key access, enforce additional security measures like multi-factor authentication (MFA), and audit key usage, all without reconfiguring your SSH servers.

The number of secure shell (SSH) keys in a large enterprise can seem unmanageable. Multiple SSH keys are distributed to end-users and stored in software on workstations— and these keys are high-value targets for attackers. Additionally, many of these SSH keys are not visible to InfoSec teams and therefore are challenging to audit.
Improperly protected secure shell (SSH) keys can be compromised, granting unauthorized users access to critical systems.
Without central control of secure shell (SSH) keys, it's nearly impossible to audit the usage of every key or revoke user access when necessary.
Enforcing stricter security controls like multi-factor authentication (MFA) or device authentication often requires reconfiguring servers manually.
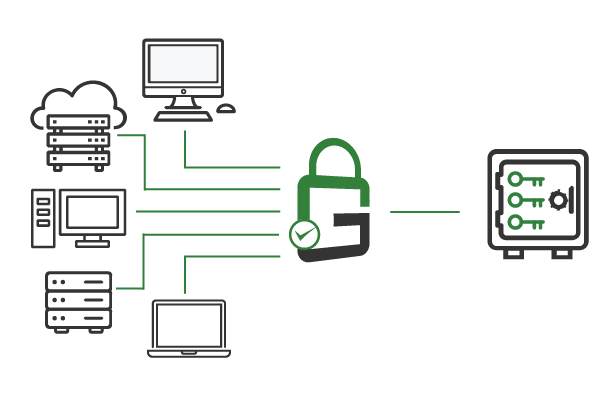
When you deploy GaraTrust, secure shell (SSH) keys remain secured and non-exportable in the HSM servers at all times. End-users receive proxied access to only the HSM keys they are authorized to use. Since keys are always protected with hardware-level security, the risk of an SSH key being compromised is minimal.
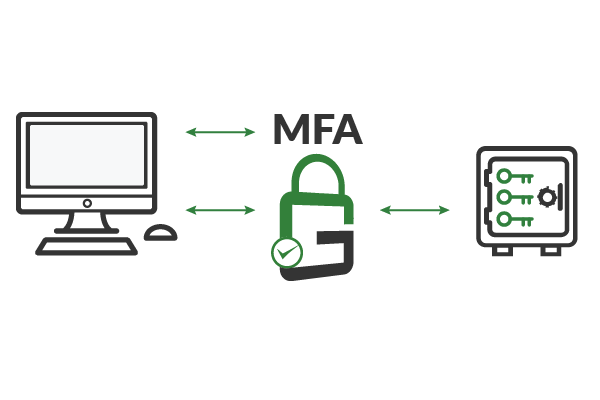
GaraTrust can integrate with existing SSH clients to transparently provide advanced cybersecurity controls, such as multi-factor authentication (MFA), device authentication, approval workflows, IP address whitelisting, notifications, and more. All within our HSM as a service. These features can be established on a per-key or per-user basis.
Since secure shell (SSH) keys are secured in the hardware security module (HSM) and centrally managed within the HSM software, SSH key management is easily auditable. Auditors can see which keys were used, at what time, and by whom. Furthermore, administrators can alter users’ permissions to the SSH keys from a single interface.
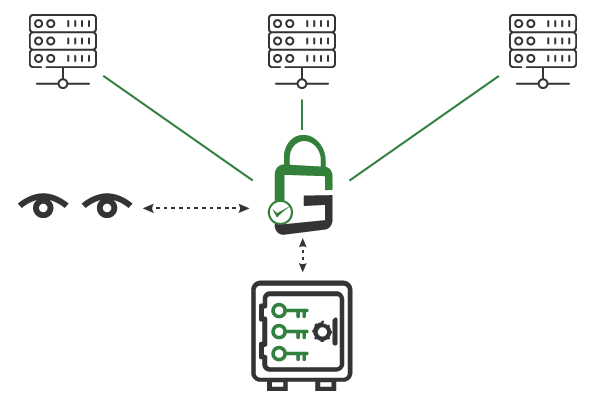
There are several benefits to using GaraTrust for secure shell (SSH) key management; they all come without installing anything on the SSH server. The first benefit is enabling just-in-time access so that administrators can only SSH to servers when there is a need to do so. The second is the seamless integration of advanced privileged access security controls, such as multi-factor authentication (MFA), device authentication, approval workflows, IP address whitelisting, and more, when authenticating to a server via SSH. The third is a centralized audit of when an SSH key is used.
It depends on the secure shell (SSH) client you are using, but it is typically done via an SSH-Agent that is capable of using hardware security module (HSM) keys managed in GaraTrust.
Yes, GaraTrust can also secure the SSH server keys in the hardware security module (HSM).
Yes, they should. Since GaraTrust integrates via an SSH-Agent, the commands should work without alteration, assuming you are using a supported client.
Since GaraTrust proxies the client key used to complete the challenge-response handshake, it can enforce additional security controls (e.g., multi-factor authentication) before it allows the use of the key. In other words, the SSH server delegates the additional privileged access security controls to GaraTrust and is unaware that the additional controls are taking place.
The need for frequent key rotation drops is drastically reduced since the keys are never exported from the Hardware Security Module (HSM). While every key eventually should be rotated, you can do so less frequently since the Secure Shell (SSH) keys are now well protected. Of course, please check with your enterprise’s policies to ensure you will remain compliant.
Schedule a demo to see how GaraTrust can improve the security and performance of cryptographic operations throughout your environment.