Integrations To All The Tools You Use
GaraTrust comes with a host of native client integrations, making it easy to deploy GaraTrust directly into your IT environment without needing to develop custom integrations.












Some of the most sensitive keys in an enterprise are the code signing keys. If improperly protected, these code signing keys can be compromised, potentially resulting in catastrophe.
Storing your code signing keys in a hardware security module (HSM) provides excellent security (and is now required per the CA/Browser Forum requirements) but may introduce integration challenges and performance bottlenecks, leaving the CI/CD pipeline clogged. On the other hand, storing your code signing keys outside of an HSM significantly increases risk and may put your code signing solutions out of compliance.
GaraTrust gives you the best of both worlds: strong enterprise code signing security and superior performance, plus client integrations to all the cybersecurity tools used in your environment today.

The ramifications of insecure code signing practices can be disastrous. Code signing keys must be secured at all times.
But code signing best practices & security isn’t the only thing that matters— an enterprise code signing solution must also account for performance and ease of use. In a DevOps environment, speed is paramount: code signing must not slow down the CI/CD pipeline. At the same time, the code signing solution must integrate with existing enterprise cybersecurity tools and processes for ease of deployment, use, and management.
Code signing keys are mission-critical assets and must be protected with the highest level of security at all times.
Enterprises continuously integrate and sign code, so an enterprise code signing solution must provide extremely fast signatures.
If your code signing tools aren't integrated with your hardware security module (HSM), deploying a fast and secure enterprise code signing solution at scale is challenging.

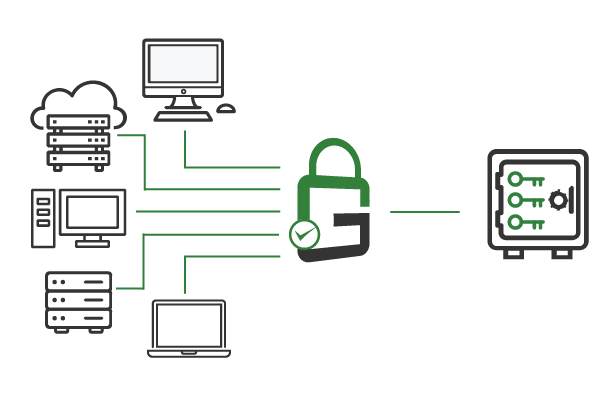
GaraTrust is deployed on customer-managed infrastructure between the hardware security module (HSM) and the signing clients, restricting those signing clients to proxied key access.
The result is that all code signing keys remain secured and non-exportable in the HSM at all times, providing maximum security, while end-users can still use the keys they need to efficiently sign code.
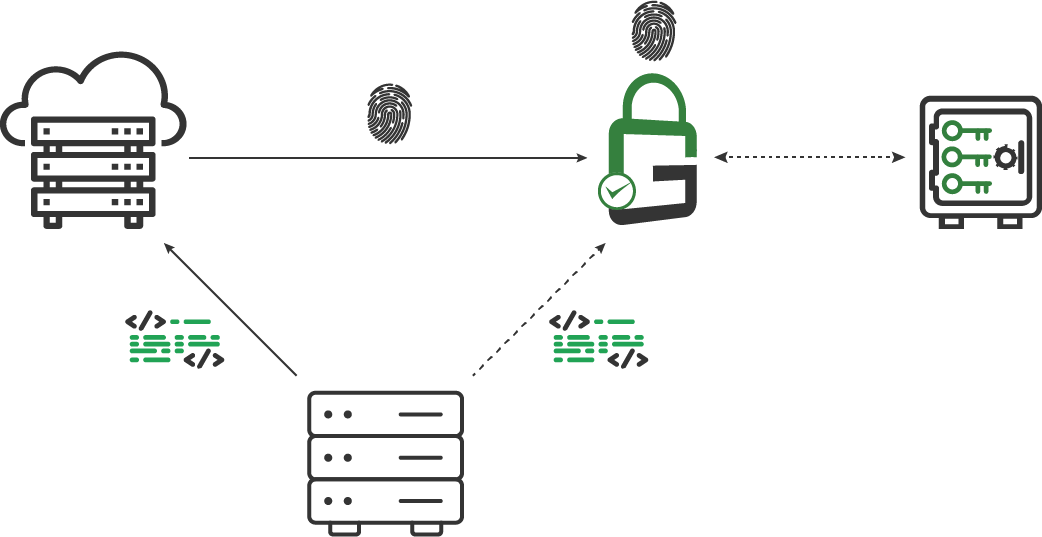
GaraTrust uses a client-side hashing architecture. Signing clients hash the code they need to sign before sending it over the network to create the signature.
This hash signing architecture limits the amount of data being transmitted over the network, so secure code signing stays fast to support continuous integration while the signing keys remain secured in the hardware security module (HSM).
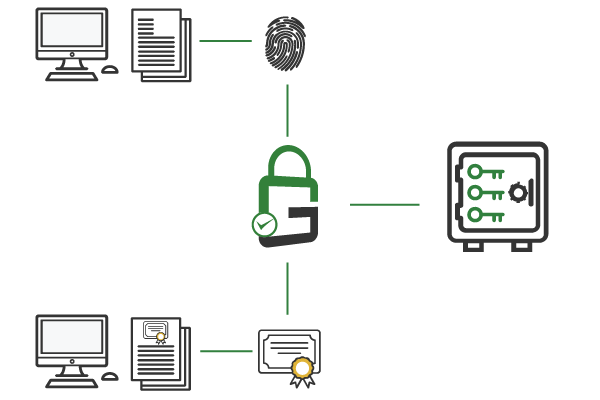
GaraTrust supports advanced security features, including multi-factor authentication (MFA), device authentication, approval workflows, IP address whitelisting, notifications, privileged identity management (PIM) and more. With GaraTrust’s granular controls, these features can be enabled on a per-key or per-user basis and integrated with any signing tool.
With client-side hashing in place, GaraTrust receives only the hash to sign during the code signing process. To ensure that the digital signature hash it receives matches the digital signature hash of the code in the repository, GaraTrust automatically retrieves the source code, performs a deterministic build, and independently generates a hash. A precise match of the two digital signature hashes proves that the code signing has not been tampered with, preventing malware injections and supply chain attacks.
GaraTrust comes with a host of native client integrations, making it easy to deploy GaraTrust directly into your IT environment without needing to develop custom integrations.












Yes, GaraTrust supports native signing tools that can be executed from any CI/CD pipeline.
Yes, GaraTrust supports native signing tools that can be executed from a developer’s workstation.
GaraTrust can support certificates from any certificate authority via its most basic certificate processing capabilities. For automated certificate issuance, GaraTrust has first class support for certain certificate authorities.
For manual production code signing (typically done as a ceremonial process), GaraTrust supports multi-factor authentication (MFA), device authentication, quorum-based approval workflows, automated hash validation, IP address whitelisting, just-in-time access, audit notifications, and granular key permissions.
For automated code signing, GaraTrust supports device authentication, automated hash validation, IP address whitelisting, audit notifications, and granular key permissions.
One of GaraTrust’s most advanced cybersecurity controls is its patented Automated Hash Validation feature. This feature uses reproducible builds to ensure that what is being signed matches what is in the source control repository. By doing this, compromising the build server alone is not sufficient for an attacker to get their malware signed. The attacker must commit the malware to the source code repository. Not only is this an additional attack that the attacker must be capable of, it also leaves a permanent record of the attack that should get detected during code review or scanning.
GaraTrust supports two modes of Automated Hash Validation – pre-sign and post-sign. In pre-sign mode the validation is done before the code gets signed, thereby acting as a preventative control, which provides the highest level of security but also has the highest performance penalty. In post-sign mode, the validation is done after the signature is generated, thereby acting as a detective control, which has slightly reduced security benefits but great performance. In post-sign mode, even if an attacker is able to sign their malware it will be detected relatively quickly so action can be taken. Garantir recommends using pre-sign validation for production signing and post-sign validation for non-production signing that happens in the continuous integration environment.
Yes, as part of Automated Hash Validation, GaraTrust can run any set of tools on the source code and/or binaries and use the result of running those tools as part of validation. For example, GaraTrust can be configured to run static analysis tools, fuzzing tools, etc.
For very performance-sensitive customers, GaraTrust’s Automated Hash Validation feature can be used to offload processing that the build server would otherwise have to do. By doing this, tasks can be run in parallel that would otherwise run in series, thereby reducing the overall wall-clock time taken to complete a build.
There are a few reasons. The first is that all your code signing keys, including non-production, should be stored in your enterprise’s hardware security module (HSM). Even though these keys aren’t publicly trusted, they are trusted in your test environment and so they can be used to sign malware that spreads in that environment. The second is that code signing keys and build servers are high-value targets for attackers. If you are under attack you want strong protection in place and you want to be alerted to the issue as soon as possible. GaraTrust provides this for you. The third reason is that you want to have a system that manages your certificates for you. Without that, it is easy to forget that a certificate will expire which results in downtime in your CI/CD pipeline.
GaraTrust supports a quorum-based approval process where a quorum of approvers must approve the request before the signature is generated. If any approver rejects the request, the signature is not generated. GaraTrust even supports tiers of quorums with each tier having its own quorum size. For example, you could configure it so that at least three developers must approve the request. Once that is complete, at least one tester must approve it. And so on as you see fit.
Yes. GaraTrust integrates with your hardware security module (HSM) of choice to create, store, and use private keys for code signing, amongst other use cases.
Schedule a demo to see how GaraTrust can improve the cybersecurity and performance of cryptographic operations throughout your environment.