As many enterprises move away from a traditional network perimeter model and adopt a zero-trust architecture, advanced cybersecurity solutions that enable granular access controls are in high demand.
GaraTrust supports a variety of advanced cybersecurity features, including multi-factor authentication (MFA), device authentication, notifications, approval workflows, and more. These granular controls can be enforced per-key or per-user basis for any public-private key use case without manually modifying servers or applications.
Passwords often create vulnerabilities, as end-users often set weak passwords. Key-based authentication provides superior cybersecurity and should be implemented whenever possible. Store all cryptographic keys in a hardware security module (HSM) and restrict end-users to proxied key access via GaraTrust to enable seamless integrations with all clients and ensure the keys are never exported from the HSM.
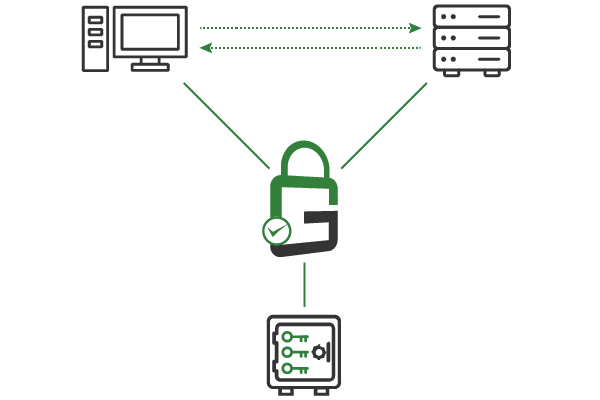
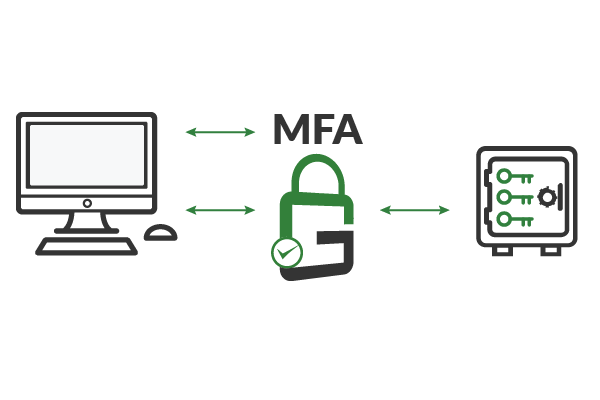
GaraTrust supports a number of granular cybersecurity controls, including multi-factor authentication (MFA), device authentication, approval workflows, and more. Clients authenticate to GaraTrust when they request to use a key, so these granular security controls can be enforced on a per-key or per-user basis without manually reconfiguring servers or applications.
When you deploy GaraTrust, cybersecurity leaders can disable select keys until it’s time to use them. Decryption keys for sensitive data, secure shell (SSH) keys for privileged systems, code signing keys for production releases, and more can all be disabled with a few clicks and enabled only when they must be used.
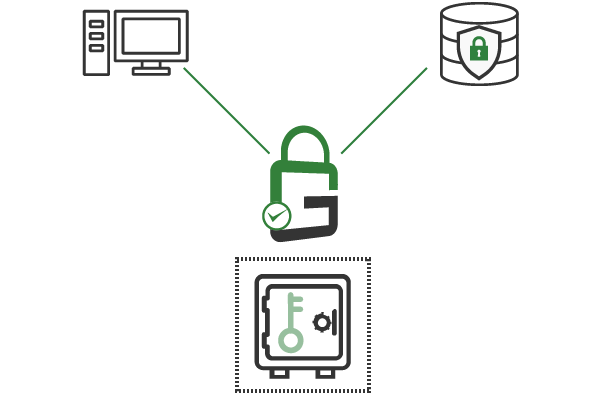
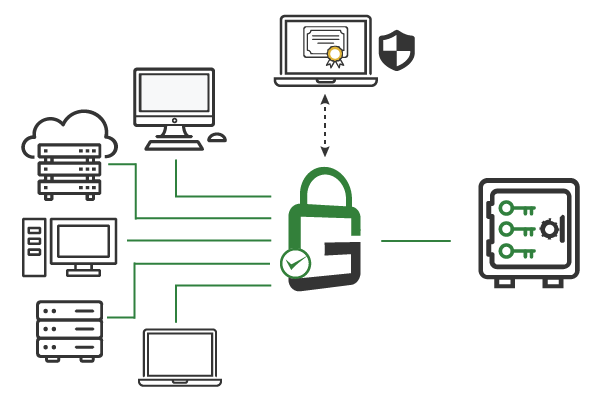
With GaraTrust, all cryptographic keys are centrally secured and managed. This makes establishing and enforcing cybersecurity policies possible with a few clicks from a single interface. Policies can be set on a per-key or per-user basis.
GaraTrust supports a zero-trust environment by making it easy to enforce granular security access controls on various enterprise assets. With all cryptographic keys secured in a centrally managed hardware security module (HSM), policies can be set per-key or per-user. GaraTrust allows customers to enforce multi-factor authentication (MFA), device authentication, approval workflows, and more to access encrypted data, production systems, critical servers, sensitive documents, and other privileged assets without reconfiguring servers or applications.
Implement secure protocols like mutual transport layer security (TLS) and secure shell (SSH) to enforce key-based authentication whenever possible.
Leave cryptographic keys disabled until seconds before an authorized and authenticated end-user needs access.
Enforce granular access security controls on every key, including multi-factor authentication (MFA), device authentication, approval workflows, notifications, and more.
Access policies can be set and enforced on a per-key or per-user basis with just a few clicks from a single interface.
GaraTrust supports single-sign on (SSO) using existing identity providers, resulting in fast adoption and easy deployment.
Audits can be conducted at any time, with detailed logs showing which keys were used, at what time, and by whom.
Schedule a demo to see how GaraTrust can improve the cybersecurity and performance of cryptographic operations throughout your environment.