Strong authentication ensures only authorized end-users access sensitive data, servers, and other enterprise assets.
With GaraTrust, customers can enforce granular security controls on a wide range of resources without needing to reconfigure servers or modify applications manually.
Username and password-based authentication are relatively easy to break via social engineering, password stuffing, or simple brute force attacks. Use protocols such as secure shell (SSH) and mutual transport layer security (TLS) to assign end-users unique digital identities and require key-based authentication whenever possible.
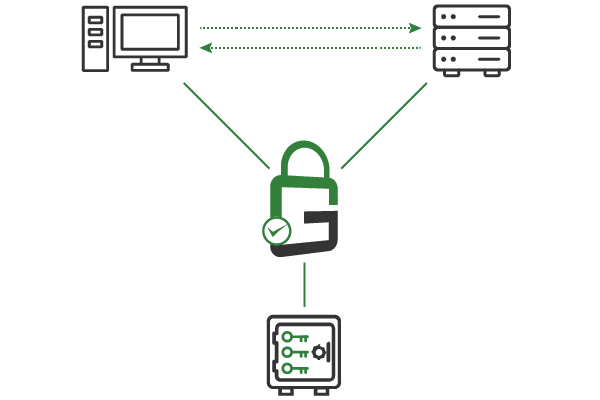
The enterprise must manage many keys and certificates when using key-based authentication via mutual transport layer security (TLS) or secure shell (SSH). To simplify management and strengthen cybersecurity, all private keys should be stored in a centralized hardware security module (HSM) or key manager.
When a client needs to use a particular key, they send the request to GaraTrust. GaraTrust authenticates the client before interfacing with the hardware security module (HSM) to perform the private key operation. As a result, the private keys always remain secured and granular security controls are easily enforced.
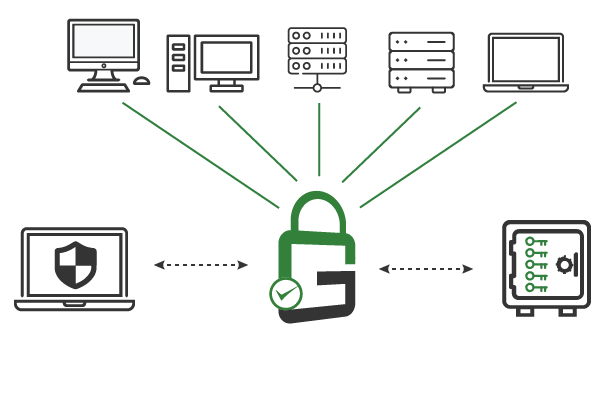
GaraTrust supports a number of granular controls, including multi-factor authentication (MFA), device authentication, approval workflows, and more. Because clients authenticate to GaraTrust when they need to use a key, these granular controls can be enforced on a per-key or per-user basis with a few clicks from the GaraTrust interface. There’s no need to reconfigure servers or applications.
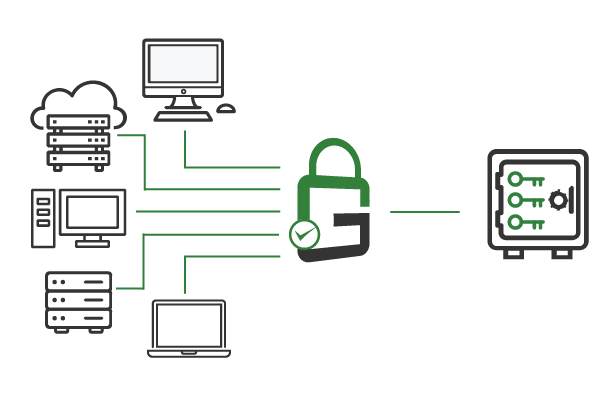
GaraTrust secures all digital identities and cryptographic keys in a centrally managed hardware security module (HSM). Authorized end-users can use the keys as needed by sending the request to GaraTrust, which then authenticates the client according to the policy in place. GaraTrust allows customers to enforce granular controls, like multi-factor authentication (MFA) and device authentication, without needing to reconfigure servers and applications manually.
Enforce multi-factor authentication (MFA), device authentication, approval workflows, notifications, IP address whitelisting, and more.
Cryptographic keys and identities are always stored in a non-exportable manner in a certified hardware security module (HSM) or key manager.
All access controls can be enforced on a per-key or per-user basis with a few just a few clicks. No reconfigurations required.
Because all cryptographic keys are centrally managed and secured, policy can be set and enforced from a single interface.
GaraTrust supports single-sign on (SSO) using existing identity providers, resulting in fast adoption and easy deployment.
Audits can be conducted at any time, with detailed logs showing which keys were used, at what time, and by whom.
Schedule a demo to see how GaraTrust can improve the cybersecurity and performance of cryptographic operations throughout your environment.