Every enterprise is undergoing a digital transformation, with many applications and databases being shifted from legacy infrastructure to the cloud.
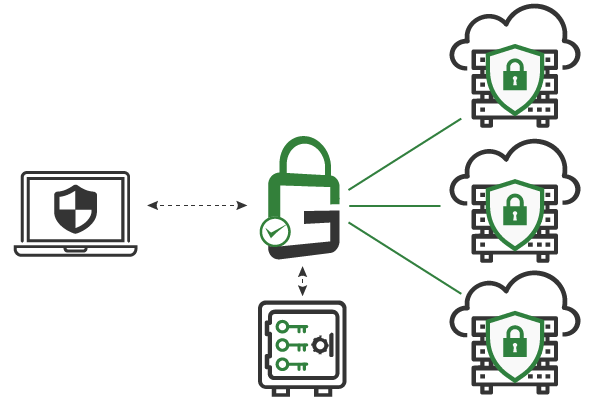
GaraTrust supports multiple aspects of cloud security, whether using a private cloud, a public cloud with a third-party cloud provider, or a hybrid environment of both on-premises and cloud infrastructure.
It is best practice to cryptographically timestamp your data before encrypting it and uploading it to the cloud. This allows you to quickly identify if the data has been tampered with at any point in time. GaraTrust integrates with all major trusted timestamp authorities (TSA) to support cryptographic timestamping seamlessly.
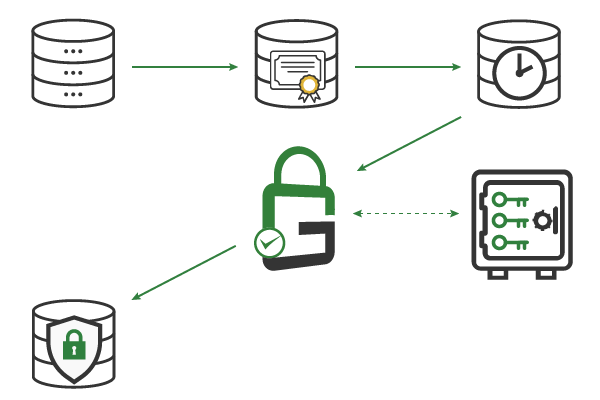
Whenever possible, encrypt data at rest using a self-managed (i.e., on-premise) Key Management Service (KMS). This is especially important when the third-party is the one storing the data, as is the case with cloud providers. By encrypting the data before it is sent to the storage provider, you benefit from the storage provider’s scale without sacrificing the confidentiality or integrity of your own data.
When encrypting data before uploading it to the cloud, be sure to use a bring-your-own-key (BYOK) approach. This enables you to retain control over your data while the decryption keys stay secured in a centrally managed hardware security module (HSM). GaraTrust enables authorized and authenticated end-users to use the decryption keys without the keys ever needing to leave the confines of the HSM.
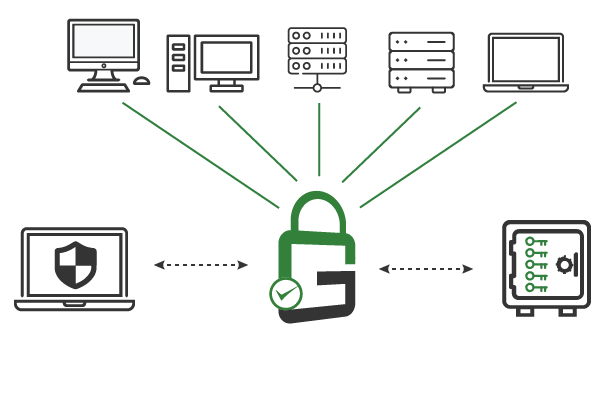
Ensure that only authorized and authenticated end-users can use the keys needed to access encrypted data in the cloud. GaraTrust supports granular access controls, such as multi-factor authentication (MFA), device authentication, and approval workflows, on a per-key or per-user basis.
When you deploy GaraTrust, you can cryptographically timestamp, digitally sign, and encrypt all data prior to uploading it to the cloud. All cryptographic keys are generated and secured within a centrally managed hardware security module (HSM). Authorized end-users can use the keys without exporting them from their secure storage. Cybersecurity leaders can enforce granular access controls on a per-key or per-user basis from the GaraTrust interface.
Cryptographically timestamp, digitally sign, and encrypt all data before uploading it to cloud storage.
Generate and store all cryptographic keys in a non-exportable state in certified hardware security module (HSM) or key manager.
Enforce granular access on cryptographic keys, including multi-factor authentication (MFA), device authentication, approval workflows, notifications, and more.
Establish and enforce key policies on a per-key or per-user basis with only a few clicks from a single centralized interface.
Use any infrastructure that fits your needs, including on-prem, private cloud, public cloud, and hybrid environments.
Conduct audits at any time to see which keys were used, by whom, and when, simplifying compliance with data security regulations.
Schedule a demo to see how GaraTrust can improve the cybersecurity and performance of cryptographic operations throughout your environment.