By now, you’ve probably come across at least a couple articles highlighting the benefits of migrating to a zero trust (or an SDP zero-trust) architecture. These articles are correct— you should be looking to migrate to some form of zero-trust in your environment, if you aren’t already. But the reality is it takes time to plan, deploy, test, and document a zero-trust implementation, and to train your employees on how to use it.
So, while you may already be somewhere along your journey in migrating to zero-trust, you’re most likely stuck with your existing Virtual Private Network (VPN) infrastructure for a period of time. You need to secure your VPN as well as possible until the transition to zero trust is complete. But with the high number of people working from home these days, you can not afford for your VPN to go down.
So the question becomes:
How can you secure your VPN effectively during the migration to zero trust—without disrupting users or investing heavily in technology you plan to replace?
This post outlines a simple approach most VPNs already support, followed by an advanced method for organizations seeking even greater security.
High-Level Threat Model
Beyond encrypting data in transit, VPNs play a major role in authentication and authorization. At a high level, your VPN is responsible for preventing:
Unauthorized users from accessing enterprise resources
Access from untrusted or unmanaged devices
Valid users accessing resources they shouldn’t
These situations typically arise after:
Stolen Credentials
Passwords, client certificates, or private keys are compromised.
Stolen Device
An attacker gains physical control of a user’s laptop or mobile device.
Compromised Device
Malware or an attacker gains remote control of a user’s device.
Lateral Movement (Pivoting)
A user accesses one resource legitimately, then attempts to reach others that should be restricted.
To mitigate these threats, VPNs commonly apply controls such as:
Multi-Factor Authentication (MFA)
Device authentication
Resource Access Control Lists (ACLs)
Threat analysis (behavior, geolocation, time-of-day patterns, etc.)
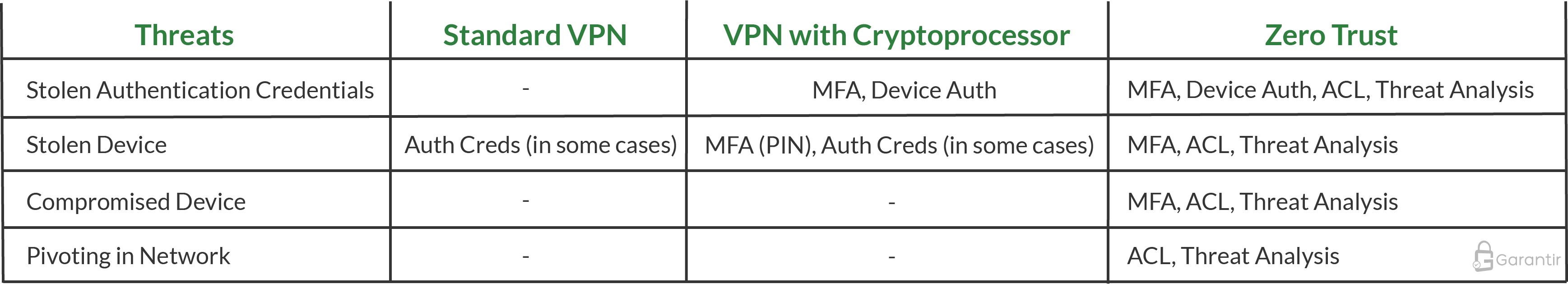
Comparing VPN To Zero Trust
Assuming a standard VPN with basic configuration (e.g., no MFA in place), the security comparison between a VPN and Zero Trust implementation is shown below:

Enhancing VPN Security
Because VPNs operate as perimeter-based systems, it’s not practical to implement granular resource controls solely at the VPN level. However, you can still add meaningful protections by implementing:
MFA
Device authentication
Basic threat analysis
One option is upgrading your VPN configuration or integrating a third-party MFA provider. While effective, this can be expensive and may impact usability if not deployed carefully.
Fortunately, there is another approach—one that is free, easy to deploy, and supported by almost all VPNs:
Client-Certificate Authentication
Client-certificate authentication alone does not deliver MFA or device authentication. But when combined with a secure cryptoprocessor, it can.
A cryptoprocessor is a hardware component that securely stores private keys, similar to a miniature HSM built into a device. Today, most client devices already include one:
Windows/Linux: TPM
macOS: T2 chip
Android: Hardware-backed Keystore
iPhone/iPad: Secure Enclave
Because the private key is non-exportable and tied to the device, the certificate effectively becomes a device authentication factor. Many cryptoprocessors also require a PIN, which acts as “something you know,” enabling basic MFA.
This provides:
Stronger protection against credential theft
Device binding without additional hardware
Improved security using technology most organizations already have
It’s important to note that while this MFA is helpful, it does not fully protect against compromised devices since the PIN is typically static—unlike modern MFA methods (TOTP, FIDO2, etc.) that zero trust systems commonly use.
Still, this approach improves security significantly without changing your VPN’s server-side configuration.
When Devices Lack Cryptoprocessors
Some devices, including virtual machines or legacy hardware, may not have an embedded cryptoprocessor. Options include:
vTPM for virtual machines that support it
External cryptoprocessors such as smart cards or security keys
These are affordable and provide additional hardware-based protections.
Advanced Configuration
For additional security, the deployment model described above can be advanced by storing the client private keys in a centrally-managed hardware security module (HSM). Then, by way of a secure HSM-proxy like GaraTrust, end-users get proxied access to their client-certificate authentication keys, instead of having direct possession of them.
Since GaraTrust supports very advanced authentication including (non-static) MFA, device authentication, approval workflows, behavior analysis, and more, your VPN automatically reaps the security benefits without any change to your VPN configuration.
Strengthen Your VPN While Preparing for Zero Trust
If your organization is still working through its migration to zero trust, Garantir can help secure your VPN environment during the transition. Our professional services team can assist with key protection, authentication enhancements, and risk mitigation.
To maximize long-term security, storing private keys in enterprise-grade HSMs is essential. GaraTrust makes this easy by offering:
Fast proxied key access
Secure non-exportable key workflows
Extensive native integrations
Support for modern authentication and cryptographic use cases
Get in touch with our professional services team to help d shore up your VPN’s security while you migrate to zero trust.


