Quantum computing is no longer just a futuristic concept; it’s swiftly becoming a real threat to the security protocols we rely on today. This shift raises an urgent question: how do we protect our software and systems from attacks enabled by powerful quantum machines? The answer lies in adopting post-quantum cryptography (PQC), a new generation of encryption and digital signature algorithms designed to withstand these emerging threats.
The U.S. NSA has introduced CNSA 2.0, a clear roadmap for moving toward quantum-resistant security standards. In this guide, we’ll break down what CNSA 2.0 means for code signing, why switching to post-quantum algorithms is critical, and how organizations can start preparing for this transformative shift.
The Quantum Threat to Modern Cryptography
Quantum computers pose a significant risk to the encryption techniques we depend on today. Algorithms like RSA and elliptic-curve cryptography (ECC) rely on mathematical problems that are practically unbreakable with classical computers. However, a sufficiently advanced quantum machine could solve these problems efficiently, making current cryptographic safeguards vulnerable.
This potential isn’t just theoretical. Experts warn that adversaries might already be collecting encrypted data now, thinking of it as stockpiling information that could be cracked once quantum computing matures. For digital signatures and code signing, the stakes are especially high: these mechanisms verify software legitimacy and integrity. If quantum attackers can forge signatures, the entire trust chain, software updates, firmware, even official documents, could be compromised.
What Is Post-Quantum Cryptography?
Post-quantum cryptography, or PQC, involves developing algorithms that remain secure even against quantum attacks. Unlike quantum cryptography, which leverages quantum physics for secure key exchange, PQC algorithms run on classical hardware but are built upon complex mathematical problems that quantum algorithms can’t easily solve. Essentially, PQC aims to replace our existing cryptographic tools with quantum-safe alternatives.
The National Institute of Standards and Technology (NIST) has been leading efforts to evaluate and standardize these algorithms. Last year, they selected several schemes, including ML-KEM (CRYSTALS-Kyber) for encryption and key exchange, and ML-DSA (CRYSTALS-Dilithium) for digital signatures, both of which are poised to be widely adopted in the near future. These algorithms are designed to be efficient and secure, making them suitable for a variety of applications, from encrypting data to signing code.
CNSA 2.0: A Roadmap for a Quantum-Resistant Future
Responding to the escalating quantum threat, the NSA launched CNSA 2.0, an updated set of guidelines and approved algorithms intended to secure U.S. national security systems. Announced in late 2022, CNSA 2.0 lays out specific deadlines for organizations to adopt quantum-resistant encryption methods, emphasizing that early action is crucial.
Key highlights of CNSA 2.0 include:
- Digital Signatures for Software and Firmware: Now explicitly recommending hash-based, quantum-safe signatures like LMS (Leighton-Micali Signature) and XMSS (Extended Merkle Signature Scheme). These are considered robust and suitable for secure code signing, but they require careful key management due to their stateful nature.
- General Signature Algorithms: Preparing for the adoption of lattice-based schemes like ML-DSA, which are stateless and easier to manage over the long term.
- Post-Quantum Key Exchange: Using algorithms like ML-KEM for encrypting keys exchanged during protocols like TLS or VPNs, complemented by strong symmetric encryption like AES-256 and hashes like SHA-384/512 for added security.
What algorithms are being phased out? Traditional RSA and ECC are being gradually replaced, and their use will be discontinued in U.S. government systems by 2030. Meanwhile, less vetted schemes like SPHINCS+ or Falcon are not included in CNSA 2.0, primarily due to concerns over practicality and risk.
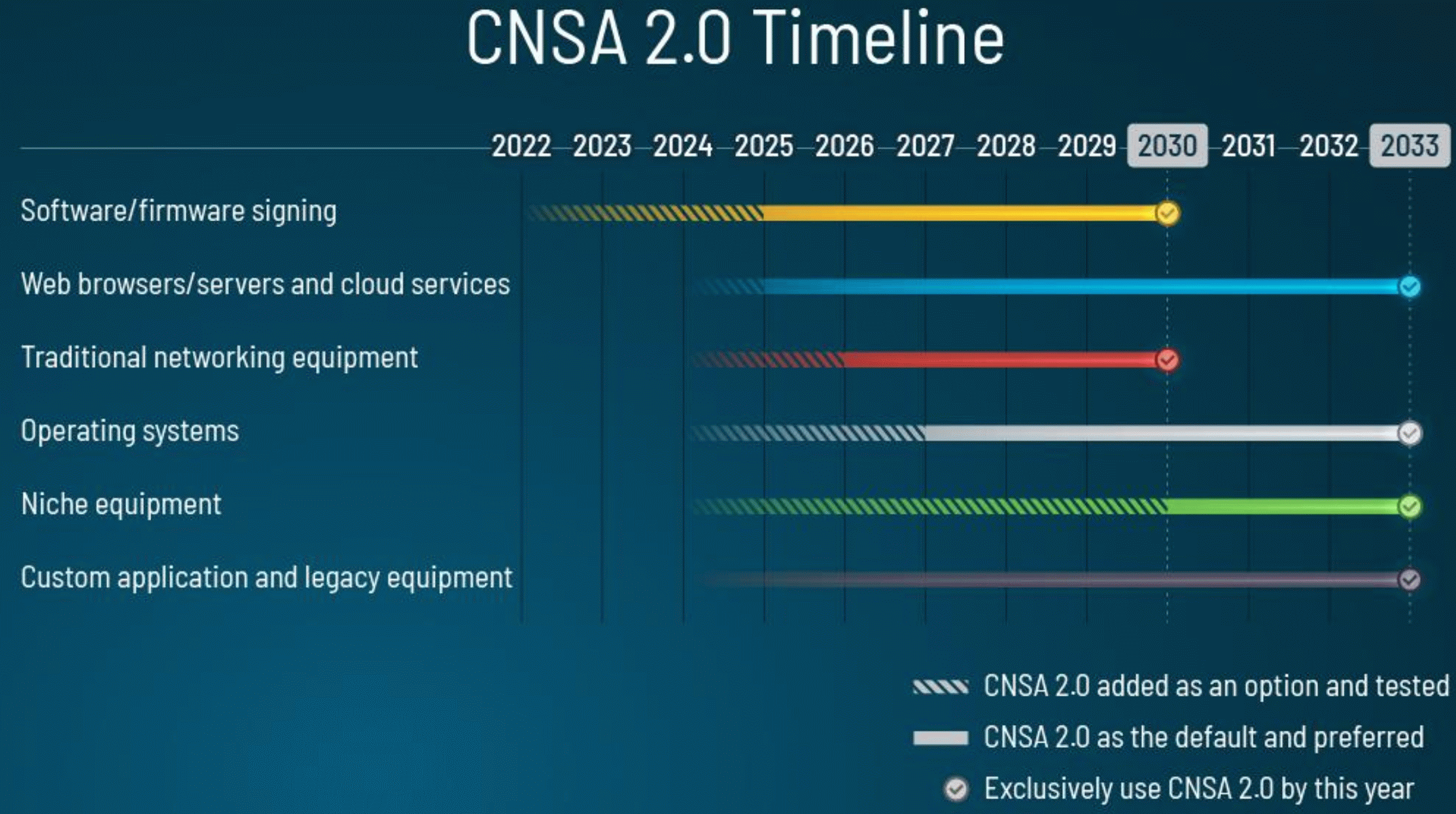
Timeline: When Do You Need to Act?
CNSA 2.0 sets a clear schedule:
- Code and firmware signing: Transition should begin immediately; by 2025, CNSA algorithms are preferred, and by 2030, they are mandatory.
- Web and cloud communications: Support for post-quantum algorithms by 2025, with full adoption by 2033.
- Network devices and operating systems: Support should be in place by 2026-2027, with full transition by 2033.
- Legacy systems: Upgrades or replacements are expected through 2033.
The emphasis is on getting ahead, particularly for critical components like code signing, since they establish a “root of trust.” The NSA stresses that firmware and software signatures must evolve quickly; otherwise, the entire security chain risks being undermined. Implementing quantum-safe code signing today is essential, as it forms the foundation upon which other security measures depend. By 2035, full migration in U.S. national security systems is anticipated, with older algorithms phased out entirely.
Delving Into Post-Quantum Signatures: LMS, XMSS, and More
Let’s explore the primary algorithms for quantum-resistant code signing:
- LMS (Leighton-Micali Signature): A hash-based, Merkle-tree signature scheme that’s standardized and approved by CNSA 2.0. It’s highly secure, relying solely on the strength of hash functions like SHA-256. However, it’s stateful, meaning each private key can only generate a limited number of signatures, requiring meticulous key management.
- XMSS (Extended Merkle Signature Scheme): Similar in concept to LMS, XMSS uses hash-based trees and is also stateful. It offers strong security and flexibility, with all parameter sets approved for software and firmware signing. Like LMS, it demands careful tracking of key usage.
- ML-DSA (Dilithium): A next-generation, lattice-based signature scheme that’s stateless, which simplifies key management. It provides smaller signatures and faster verification. CNSA 2.0 designates Dilithium at the highest security level, but widespread support and validation are still progressing, with expected deployment around 2025.
Challenges and Considerations
Transitioning to post-quantum signatures isn’t without obstacles:
- Larger Signatures & Keys: Hash-based signatures like LMS can produce signatures tens or hundreds of kilobytes, much larger than RSA or ECDSA. This can affect software update sizes and storage, especially on resource-constrained devices.
- Performance Impacts: Verification speed, particularly for hash-based schemes, may be slower on low-power or embedded devices. Ensuring systems can handle larger signatures or optimizing verification processes might be necessary.
- Key Management: For stateful schemes, strict key usage policies and secure storage are vital. HSM support for PQC keys will become increasingly important to maintain security and operational efficiency.
- Compatibility & Interoperability: Updating your PKI, certificates, and software signing tools to support new algorithms is critical. Some existing tools may require patching, and transitional strategies like hybrid signing, combining classical and quantum-safe signatures, may ease compatibility issues temporarily.
- Regulatory and Certification Hurdles: Using PQC algorithms in government or regulated sectors can involve stringent validation, including hardware certifications and adherence to standards like FIPS. Planning for these requirements ensures smoother upgrades.
- Legacy Systems & Backward Compatibility: During transition phases, some systems may only support legacy algorithms. Strategies such as dual-signing or phased rollouts can help bridge this gap while minimizing risk.
Practical Steps for a Smooth Transition
To prepare effectively, organizations should:
- Conduct an Inventory and Risk Assessment: Map all digital signing points, software, firmware, communications, and prioritize the most critical assets that require immediate post-quantum protection.
- Stay Updated on Standards: Monitor developments from NIST, NSA, and industry groups. As algorithms become standardized and validated, integrate them into your toolkit.
- Design for Crypto-Agility: Ensure your infrastructure can easily swap algorithms. Use flexible protocols, updatable software, and modular architectures.
- Start Testing Early: Pilot post-quantum signatures in controlled environments. Sign test files, verify compatibility, and assess performance impacts now, rather than waiting.
- Collaborate with Vendors: Engage with hardware, software, and cloud providers to confirm roadmap support for PQC. Verify their offerings align with your timelines and compliance needs.
- Implement Phased Rollouts: Begin with dual-signing or signing non-critical components. Gradually transition to full adoption, phasing out legacy algorithms over time.
- Ensure Secure Key Management: Use HSMs or other secure hardware for PQC keys. Follow best practices to prevent key reuse and protect private keys at all costs.
- Communicate Clearly: Inform stakeholders, vendors, and end-users about changes. Provide documentation and guidance on new signature standards to foster trust and smooth adoption.
Partnering for Success with Garantir
Facing this transition head-on can seem daunting, but cooperation and expert guidance make the process smoother. At Garantir, we specialize in empowering organizations to upgrade their cryptographic systems seamlessly, incorporating both classical and post-quantum algorithms. Our solutions, like GaraSign, are built to support a wide range of cryptographic protocols and are designed with crypto-agility in mind, allowing you to incorporate emerging PQC standards smoothly. This means you can future-proof your code signing processes and overall security infrastructure, reducing operational disruptions.
What we recommend:
- Stay connected with industry standards and participate in ongoing development discussions to remain ahead of regulatory and technological shifts.
- Focus on adopting flexible cryptographic solutions that can adapt easily to new algorithms.
- Engage with trusted vendors and platforms that support PQC integration, ensuring your tools evolve alongside the standards.
Why Act Now?
The reality is, the quantum threat isn’t a distant concern, it’s a present challenge that demands proactive planning. Early adoption of post-quantum signatures not only ensures compliance but also demonstrates your commitment to security and trustworthiness. Waiting until the last minute could leave your systems vulnerable or lead to costly, disruptive upgrades.
By starting now:
- You gain valuable experience and identify potential technical hurdles early.
- You secure your supply chain and software distribution channels against future threats.
- You build confidence among your stakeholders and customers regarding your security posture.
Final Thoughts
Transitioning to post-quantum code signing is more than a technical upgrade—it’s a strategic investment in your organization’s long-term resilience. While post-quantum cryptography (PQC) is a critical piece of the puzzle, it doesn’t stand alone. A truly secure software supply chain also requires alignment with CNSA 2.0 guidelines, compliance with CA/Browser Forum rules, and a holistic approach to cryptographic policy and infrastructure.
CNSA 2.0 provides a clear roadmap, with defined timelines and approved quantum-resistant algorithms. Acting now not only ensures smoother adoption but also strengthens your security posture against both current and future threats.
At Garantir, we’re committed to helping organizations embrace this new era with confidence. Whether you’re designing a new cryptographic architecture or upgrading existing systems, our expertise and solutions, like GaraTrust, support a seamless transition toward quantum-ready security.
Let’s future-proof the software supply chain—together. The time to act is now.