Ensuring the security and performance of digital signatures is a top priority for every InfoSec and DevSecOps leader. With many businesses shifting to a remote work environment due to the ongoing global pandemic, this task is made considerably more difficult.
How do you ensure the security of all digital signatures throughout a fully remote workforce, without compromising on performance?
Digital Signatures For Distributed Teams
As many companies enact work-from-home policies to keep team members safe in the midst of the COVID-19 pandemic, achieving both ironclad security and top-notch performance of digital signatures for a geographically-distributed team is now critical to business operations.
When it comes to enabling digital signatures for a distributed team, there are three general approaches:
- Keep the private keys in software and distribute to team members as needed.
- Place the keys in hardware protection (i.e. a hardware security module) and distribute many HSMs out to the various teams of your business.
- Store the keys in a centrally-managed HSM and give proxied access to all end users.
Option 1 presents major security risks and shouldn’t be considered by any company that values its data security. When signing keys are stored in software, the level of protection around them is simply too weak for comfort. Attackers could gain access to the keys by compromising an employee’s device or extracting the keys from the software itself.
Option 2 offers improved security compared to the first approach, but it comes with a daunting price tag. Hardware security modules are costly so purchasing multiple HSMs is not the most cost-effective approach to enabling secure digital signatures for a large team. Moreover, keeping multiple hardware devices synchronized and performing key management across several HSMs is a very challenging task.
Option 3 is the optimal solution, if it can be done while maintaining excellent performance. This is where hash signing comes into play.
What Is Hash Signing?
The term “hash signing” can be confusing because virtually all digital signature schemes make use of some form of cryptographic hash function.
In general, a digital signature is produced by hashing the document or code that needs to be signed, then applying the cryptographic private key operation on the resulting hash value. Since cryptographic hash functions deterministically produce a small, fixed-length output from a data input of arbitrary size, the hash serves as an electronic fingerprint of the data. The hash of the data is one component of that data’s digital signature, enabling verifiers to easily detect if any changes have been made to the document or code after the signature is completed.
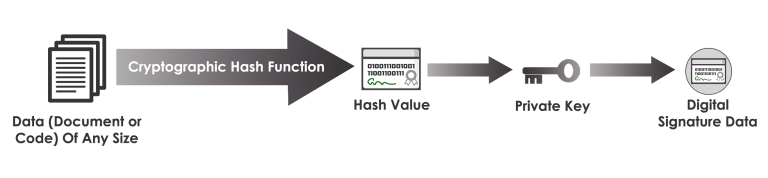
Note that the private key is not needed in the digital signature process until after the data is hashed. As such, it isn’t necessary to send all data to a signing server in order to create a digital signature. Instead, hashing can be performed locally, with only the hash value being sent to the signing server to complete the digital signature with the private key operation.
This client-side hashing method, known as hash signing, greatly improves the performance of remotely-generated digital signatures.
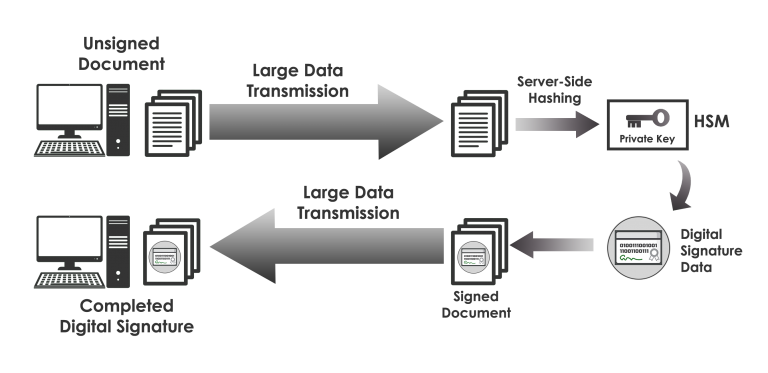
Without hash signing, companies opting for Option 3— that is, storing all private key material in centrally-managed HSMs— must upload all of the data being signed to the central signing service, then download the entire signed package once the signature is complete. For any use case that requires creating signatures for large files (e.g., code signing, document signing, cryptographic time-stamping of backups, etc.) this means it’s necessary to transport large volumes of data over the network twice, resulting in slow signature generation and unnecessary bandwidth consumption.
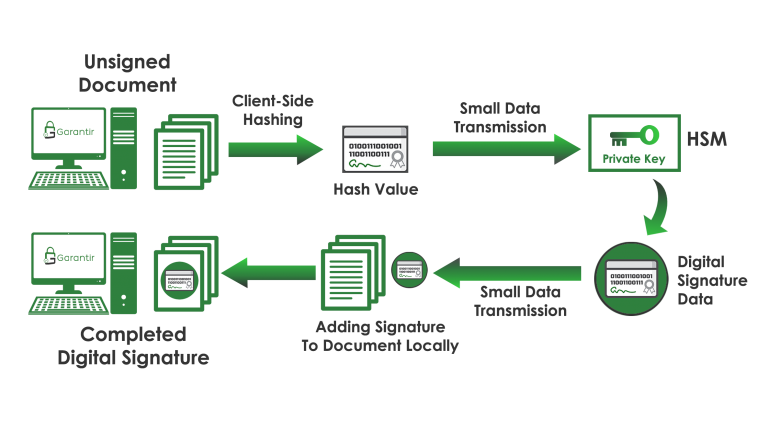
With hash signing properly implemented, this issue is resolved. Since only the hash of the data being signed is sent over the network to the signing server, bandwidth transmissions are kept to a minimum and the digital signature process is accelerated.
Challenges with Hash Signing
While hash signing offers significant advantages in terms of digital signature performance, it also comes with a few challenges. In particular, there are two major challenges with hash-based signing: client integrations and security.
Client Integrations
Many signing tools today assume that the signing key resides on the local computer the tool is being executed on. Similarly, hardware security module (HSM) APIs default to assuming the data that needs to be signed resides on the machine that is directly connected to the HSM. Of course, the former scenario presents major security risks, while the latter is not the case with hash signing.
Deploying a client-side hash signing architecture with existing tools, all while keeping the signing keys securely locked away in an enterprise HSM or key manager, is an extremely complex task. It requires a lot of low-level development work from cryptography experts that transparently do all the heavy lifting for you.
Fortunately, that is exactly what the team at Garantir loves to do. We designed our flagship product, GaraSign, to come with these cryptographic providers ready to use out of the box on all major platforms including Apple, Microsoft, Java, Android, GPG, RPM, Linux, OpenSSL, and more. Whether you are signing code, documents, challenge-response handshakes, or any other type of data, GaraSign’s client integrations make this a seamless experience for your end users.
Security
With hash signing, the signing server only sees the hash of the data, not the entirety of the data being signed. As a result, the signing server cannot analyze that data very easily. To overcome this, Garantir has built several crucial features into the GaraSign platform, including:
- Strong authentication and authorization
- Approval process flows for high valued keys
- Code analysis via the source code repository for code signing
- And much more.
Ready to learn more about how GaraSign can improve the security and performance of digital signatures in your environment? Get in touch with the Garantir team. Although the GaraSign product is fully customer-managed, the Garantir team will be happy to host your proof of concept free of charge so you can experience the speed and seamless integrations of GaraSign for yourself.


