Log files provide useful data for troubleshooting and auditing purposes. However, if this data falls into the wrong hands, it may expose sensitive data and intellectual property, potentially causing compliance challenges and providing insights into vulnerabilities. For these reasons, log files must be kept secure.
GaraTrust enables you to transparently encrypt your application log files without modifying the application code, while the decryption keys are secured within the hardware security module (HSM). This approach protects the log files, protecting the data from bad actors and promoting compliance with data privacy regulations.

Maintaining application log files is essential to analyzing and troubleshooting software. However, the data in those log files detail how your application works and may even contain sensitive data subject to regulatory compliance. Most application log files are not protected, creating security risks and potentially failing to meet data privacy regulations.
Implementing log file encryption for the enterprise can be a complex process. It may involve making significant changes to the software, which is costly and time-consuming. At the same time, ensuring that authorized end-users are able to quickly and easily view the log files as needed further complicates the encryption implementation.
Applications may accidentally log sensitive data, such as PII or PCI, leading to compliance challenges if not secured.
Log files contain sensitive data about enterprise software architecture and, therefore, must be kept secure.
Modifying applications in order to implement log file encryption can be costly, time consuming, and error-prone.
Authorized end users must have a fast and easy way to access the encrypted logs when needed.
GaraTrust protects sensitive data and intellectual property by encrypting the necessary fields within your applications’ log files.
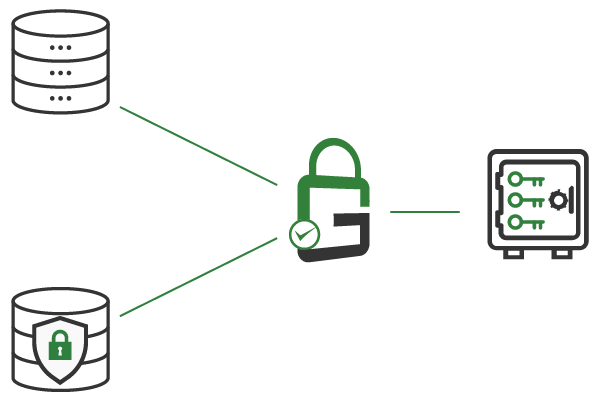
By using the public key for encryption, GaraTrust protects the application log files, regardless of which device they are generated on. By protecting the private key used for decryption in a hardware security module (HSM), GaraTrust ensures that only authorized users and systems can read the log files.
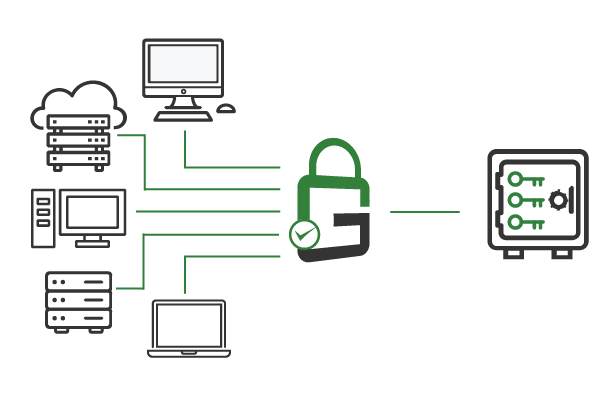
Authorized end-users are granted access to use the hardware security module (HSM)-protected private keys to decrypt the log files back to their original format. This decryption management process can be automated for integration with enterprise log aggregation platforms. Additionally, GaraTrust supports granular access controls and features, such as multi-factor authentication (MFA), device authentication, and more.
GaraTrust integrates with major logging frameworks to support transparent encryption of log files without modifying application code. For applications with custom requirements, GaraTrust provides a simple API for developers to integrate with.
Schedule a demo to see how GaraTrust can improve the security and performance of enterprise cryptographic operations throughout your environment.