- Platform
Automated Certificate Management With GaraSign
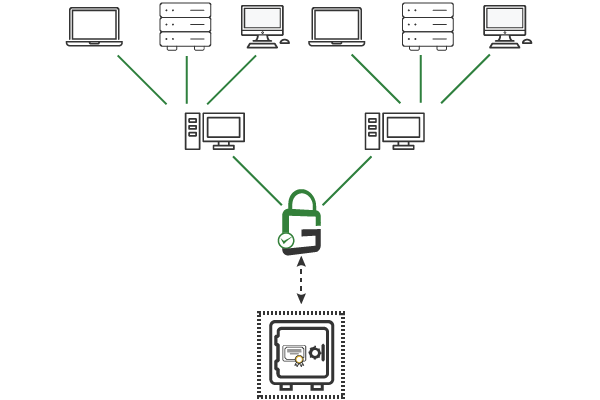
Avoid costly outages with GaraSign’s certificate lifecycle management features. These capabilities are included with any deployment of the GaraSign platform.
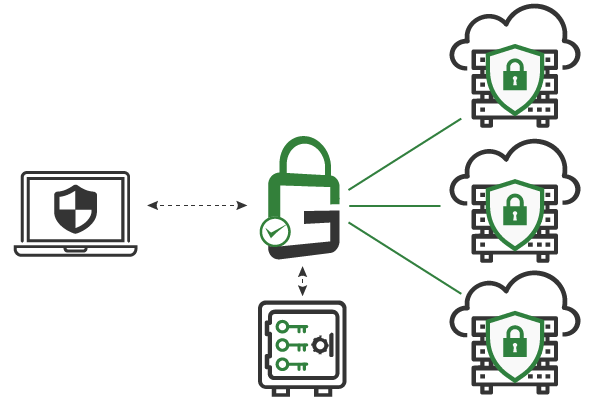
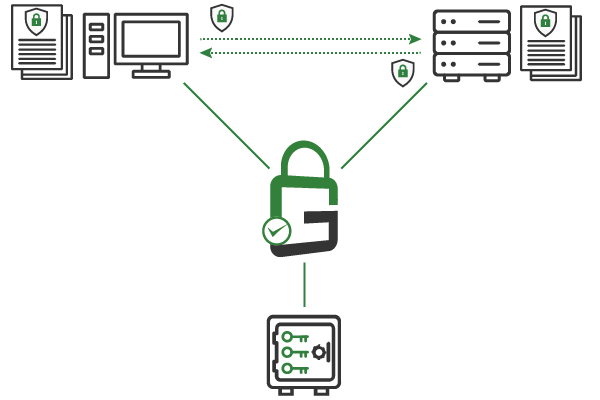
GaraSign is an integrated cybersecurity platform for the enterprise that supports a wide range of essential security functions.
- Solutions
The Garantir team has worked on the security needs of businesses of all sizes, from startups to Fortune 500 companies.
- Services
At the core of Garantir’s philosophy is the belief that securing business infrastructure and data should not hinder performance or interrupt day-to-day operations.
- Resources
Garantir is a leading cybersecurity vendor based in San Diego, California. We protect enterprise infrastructure without impeding the performance of existing business processes.
- Request a Demo